
Google warns about a phishing campaign hijacking YouTube creators with cookie stealing malware
Summary
Researchers on the Google Threat Analysis Group has been tracking the financially motivated threat actors phishing campaigning that has been targeting YouTube creators with cookie stealing malware since 2019. The threat actors have been recruiting hackers from a Russian-speaking forums offering two types of work.
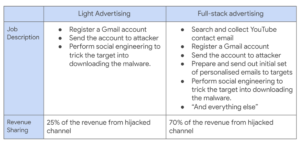
Two types of work offered
The YouTube creators are lure via social engineering attacks such as fake software landing pages and social media accounts fake software landing pages, social media account and phishing emails which will infect with information-stealing malware.
“In collaboration with YouTube, Gmail, Trust & Safety, Cybercrime Investigation Group and Safe Browsing teams, our protections have decreased the volume of related phishing emails on Gmail by 99.6% since May 2021. We blocked 1.6M messages to targets, displayed ~62K Safe Browsing phishing page warnings, blocked 2.4K files, and successfully restored ~4K accounts.” Said Ashley Shen from the Google Threat Analysis group
Cookie Stealing or pass the cookie attack is a type of session hijacking where the threat attackers access the user account with cookies stored in the browser. How the attack start is that the attackers send a phishing email asking for a collaboration from the YouTube creators. When the creators agree a URL with a fake software landing pages is sent via email or a PDF on Google Drive. The cookie stealing malware executes when the creator runs the fake software. The browser cookies on the victim’s machine will then be uploaded to the threat actor’s servers. Most malware steals both cookies and passwords.
The Malware used includes RedLine, Vidar, Predator The Thief, Nexus stealer, Azorult, Raccoon, Grand Stealer, Vikro Stealer, Masad, and Kantal, open-source malwares like AdamantiumThief and Sorano.
The hijacked YouTube channels are rebranded and used for live streaming cryptocurrency scams. While some are sold for between $3 to $4,000 based on the number of subscribers in an underground account-trading markets.
Recommendation by Google:
- Take Safe Browsing warnings seriously.
- Before running software, perform virus scanning
- Enable the “Enhanced Safe Browsing Protection” mode in your Chrome browser
- Be aware of encrypted archives
- Protect your account with 2-Step-verification (multi-factor authentication)
Reference