
How dangerous is Emotet?
March 10th, 2022 - Written By CyberLabs
Introduction
Emotet is widely considered one of the world’s most dangerous global malware families due to its role in gaining initial access to infected machines and then selling that access to other cybercriminals, such as ransomware operators. When it was first reported, a few years ago the focus was on it’s unique tiering structure and how the complex architecture both enabled resiliency against individual C2 disruptions and provided a successful malware distribution framework to rent out as a service to other actors and ransomware operators.
It was explored how network telemetry revealed that some infected Windows devices or bots were promoted via UPnP module to serve as proxy C2s, forwarding communications from newly infected devices to threat actor-controlled infrastructure. Using Lumen’s global backbone visibility to plot out the distinct clusters of C2s known as Epochs 1 and 2, and we determined that only the Bot C2s were communicating with other malware families such as TrickBot, IcedID, Qakbot, Dridex and others. At the time it was discovered that on average 40,000 unique Emotet bots daily and tracked more than 300 unique Emotet C2s in a given month. After a brief hiatus in 2019, Emotet came back full swing with a new set of bots and C2s added to its arsenal (Epoch 3). After an active couple of years, Emotet was taken offline by law enforcement in January 2021, only to resurface late last year with some initial help from TrickBot.
Current Status
This notorious Emotet botnet is unfortunately still being distributed progressively in the wild, having now blighted 130,000 systems in 179 countries. While it could be a far cry from the once global dominance of having 1.6 million devices under control, it shows that the malware is still undergoing a resurgence, and it’s getting growing every day. Threat analysts at Black Lotus labs have discussed to take a deeper jump into Emotet’s “Epoch 3” to identify new features and map it’s current distribution behaviors. As shown below, Emotet started to belatedly recreate itself in November, seeing far greater distribution via phishing campaigns beginning in January 2022.
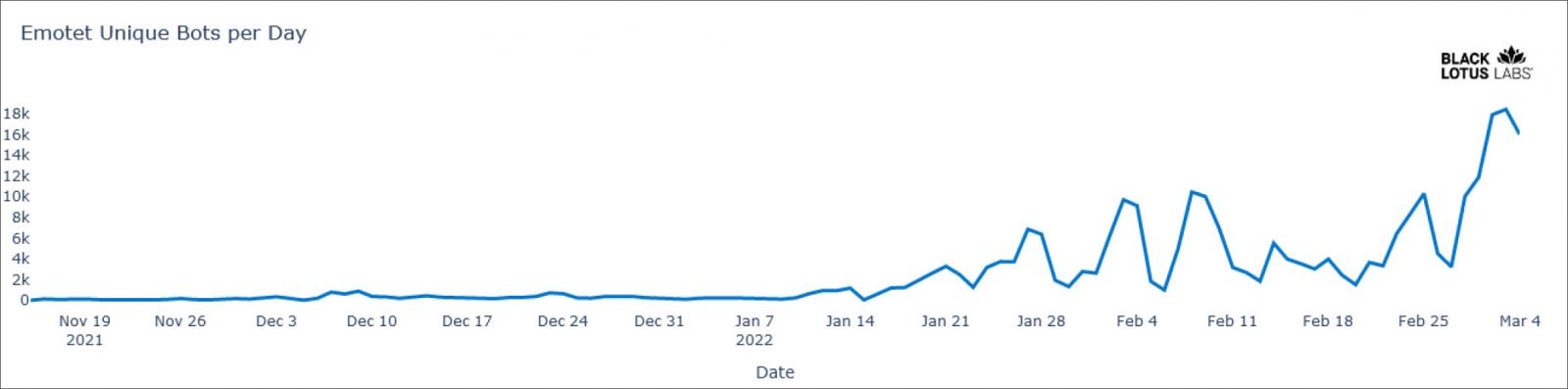
New features of the Emotet campaign also includes factors like a new elliptic curve cryptography (ECC) scheme that replaces the RSA encryption used for network traffic protection and validation. Moreover, the new version deploys a process list module only after the connection with the C2 has been established. The malware authors have now added more info-gathering capabilities for better system profiling, whereas previously, Emotet would only send back a list of running processes.
The Restructuring
Black Lotus states that there are currently 200 unique C2s supporting Emotet’s resurgence, with the number growing gradually but steadily. The average number of days of activity for C2s is presently 29. Like in previous epochs, most of their C2 infrastructure is located in the United States and Germany, followed by France, Brazil, Thailand, Singapore, Indonesia, Canada, the UK, and India. But in terms of bot distribution, the focus is Japan, India, Indonesia, Thailand, South Africa, Mexico, United States, China, Brazil, and Italy.
It is believed that the reason for the first three countries topping this list is the number of outdated and thus vulnerable Windows machines in the region. Emotet exploited a Windows AppX Installer spoofing vulnerability to install apps on the host directly from a remote source. Microsoft addressed this issue, tracked as CVE-2021-43890, with December 2021 Path Tuesday, but due to slow upgrade uptick vs. the projected benefits of keeping the abused MSIX handler, the software giant decided to simply diffuse it. But, pirated Windows copies that have purposefully severed their connectivity to Microsoft update servers remain vulnerable to malware attacks like Emotet’s.
Source:
