
The Double Clickjacking Threat
August 3rd, 2025 - Written By Cyber Labs Services
In the ever-evolving world of cybersecurity, a newly discovered exploit called DoubleClickjacking is posing a significant threat to both users and organizations. This sophisticated attack, first disclosed by security researcher Paulos Yibelo, bypasses long-standing web security defenses, targeting major platforms and putting user accounts at risk.
Traditionally, clickjackingal, so known as UI redressing, tricks users into clicking on hidden elements. Attackers typically overlay iframes from trusted websites over their own malicious pages, making users unknowingly click on the hidden iframe elements. Over the years, web browsers have introduced powerful defenses like X-Frame-Options, frame-ancestors in Content Security Policy (CSP), and SameSite cookies to block such attacks.
However, DoubleClickjacking sidesteps these protections by manipulating the brief interval between two clicks in a double-click sequence. Unlike traditional clickjacking, it doesn’t rely on iframes or cross-site requests. Instead, the attack exploits the timing between a user’s clicks, allowing attackers to swap benign UI elements for sensitive ones in the blink of an eye. As a result, the user’s second click lands on critical actions like authorizing OAuth apps, confirming transactions, or installing browser extensions all without their knowledge.
How Does DoubleClickjacking Work?
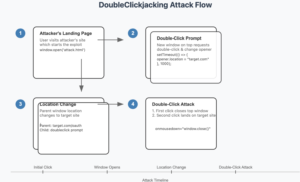
Image from Security Affairs article on DoubleClickjacking
Step 1: The Deceptive Setup
The attacker creates a seemingly innocent webpage with a button labeled something like “Double-click to verify you’re not a robot” or “Claim your reward.” Beneath or overlaying this button is an invisible iframe or window containing a sensitive action from a legitimate site, such as an OAuth permission prompt, transaction confirmation, or even a crypto wallet authorization.
Step 2: The First Click – Context Switch
When the user clicks the visible button, JavaScript triggers a window event. The top layer (like a CAPTCHA or confirmation prompt) moves or disappears, exposing the hidden sensitive action behind it. The user, unaware of the hidden content, is prompted to click again.
Step 3: The Second Click – The Exploit
The user’s second click lands directly on the now-exposed sensitive element, such as a button to allow access to an app, confirm a financial transaction, or approve a crypto transaction. In doing so, the user has unwittingly authorized a potentially harmful action, without even realizing it.
The key to DoubleClickjacking’s success lies in the timing between two clicks. Attackers use JavaScript to rapidly switch the user interface context between the first and second clicks, so the second click is executed on the hidden malicious action, rather than the button the user intended to interact with.
Why Is DoubleClickjacking So Dangerous?
- Bypasses Known Defenses
Unlike traditional clickjacking, which relies on hidden iframes or cross-site requests, DoubleClickjacking bypasses common defenses such as X-Frame-Options, SameSite cookies, and CSP because it doesn’t rely on iframes or cross-domain requests. Instead, it exploits the timing between user interactions, making it harder for security measures to detect and block.
- Minimal User Interaction Required
Unlike more complex attacks that require users to perform multiple actions, DoubleClickjacking only requires two clicks—often on familiar-looking prompts. These seemingly innocent clicks can hijack accounts or authorize harmful actions without the user realizing it.
- Broad Impact
DoubleClickjacking is capable of causing significant damage, including:
- Account takeovers
- Approval of malicious OAuth apps
- Confirmation of fraudulent financial transactions
- Installation of browser extensions
- Disabling VPNs and exposing IP addresses
All of these actions can be performed without the victim’s awareness, making the attack particularly dangerous.
Real World Scenarios
The Security researcher Yibelo demonstrated DoubleClickjacking’s effectiveness in several proof-of-concept attacks, showing successful account takeovers on platforms like Salesforce, Slack, and Shopify. The attacks also posed risks to browser crypto wallets and VPN extensions, where attackers could authorize web3 transactions or disable critical security features. These demonstrations underline the severity of the exploit and its potential impact on both personal and business security.
How Can Users and Organizations Protect Themselves?
For Users:
- Be Wary of Double-Click Prompts
Avoid double-clicking on prompts that seem unusual or unnecessary, especially those involving CAPTCHAs, reward offers, or any kind of authorization dialog.
- Keep Your Browsers and Extensions Updated
Ensure your browser and extensions are updated to benefit from the latest security patches. Browsers frequently release updates that improve security and protect against emerging threats like DoubleClickjacking.
- Use Browser Security Extensions
Install anti-clickjacking browser extensions such as NoScript or NoClickjack. These tools can help block suspicious overlays and reduce the risk of falling victim to this exploit.
For Developers and Security Teams:
- Implement Client-Side Protections
Disable critical buttons by default and only enable them after a clear user gesture (e.g., mouse movement or keypress). This helps prevent attackers from exploiting the timing between double-clicks.
- Add Confirmation Steps for High-Risk Actions
Implement extra confirmation steps for sensitive actions, such as OAuth app authorizations, transaction approvals, or account changes. This can help interrupt automated double-click exploits before they succeed.
- Monitor for Suspicious Activity
Regularly audit your website for unusual UI changes, unexpected authorization requests, or abnormal behavior that could indicate an attempt to exploit DoubleClickjacking.
- Advocate for Browser-Level Protections
Support the development of new browser standards that limit the ability to rapidly switch UI context during double-click sequences, making it harder for attackers to manipulate user actions.
Conclusion
DoubleClickjacking serves as a clear reminder that cybercriminals are constantly evolving, finding new ways to bypass existing security measures and manipulate user actions. This attack has demonstrated its ability to impact a wide variety of platforms, including major websites, browser extensions, and mobile devices. Therefore, it is essential for both users and organizations to remain vigilant. By implementing layered security defenses, regularly updating security systems, and advocating for stronger browser security standards, we can reduce the risks associated with this and other emerging threats.
Stay informed, stay secure, and always approach double-click prompts on the web with caution.
References
- https://www.reflectiz.com/blog/doubleclickjacking/
- https://www.thinscale.com/doubleclickjacking-new-exploit-can-affect-any-major-sites-security/
- https://www.bitdefender.com/en-au/blog/hotforsecurity/emerging-doubleclickjacking-threat-exploits-double-clicks-for-account-hijacking
- https://www.bleepingcomputer.com/news/security/new-doubleclickjacking-attack-exploits-double-clicks-to-hijack-accounts/
- https://www.bankinfosecurity.com/doubleclickjacking-threatens-major-websites-security-a-27203
- https://thehackernews.com/2025/01/new-doubleclickjacking-exploit-bypasses.html
- https://technijian.com/cyber-security/doubleclickjacking-the-new-double-click-attack-to-hack-websites-and-take-over-accounts/


