
Regex Gone Rogue: When One Pattern Breaks Everything
February 9th, 2026 - Written By CyberLabsServices
When a Few Characters Become a Breach
No malware was installed. No firewall was bypassed. No zero-day exploit was dropped. And yet access was granted, pipelines were triggered, and secrets were exposed.
All because of a few misplaced characters in a regular expression.
This is the quiet danger of regex misconfigurations, a class of security flaws so subtle they often pass code reviews, yet powerful enough to undermine entire security controls.
Not a bug in code. Not a vulnerability in software. A mistake in logic. And logic failures scale fast.
What Is Regex, Really?
Regular expressions, commonly called regex are pattern rules.
They decide:
- Who is allowed
- What is accepted
- What is rejected
- What gets ignored
They sit everywhere:
- Authentication filters
- CI/CD pipelines
- Web application firewalls
- Input validation rules
- Cloud automation triggers
Regex is the gatekeeper. And when the gatekeeper misunderstands the rules, the gate stays open.
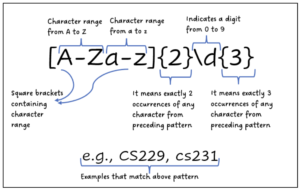
The Illusion of Safety
At a glance, a regex often looks correct.
It matches the right words, passes basic tests and behaves exactly as expected, until it doesn’t.
Unlike obvious vulnerabilities, regex failures don’t crash systems or raise alerts.
They silently expand trust boundaries.
What was meant to match one exact value suddenly matches many.
What was meant to block attackers quietly lets them through.
When Regex Becomes a Security Vulnerability
A regex misconfiguration happens when a pattern matches more than intended.
The most dangerous mistakes include:
- Missing anchors
- Overly broad wildcards
- Partial string matching
- Incorrect grouping
- Trusting regex for authorization logic
These mistakes don’t look malicious.
They look harmless.
And that’s why they’re dangerous.
RealWorld Example: When Regex Almost Broke AWS CodeBuild
A Wiz Research report revealed how a single unanchored regex in AWS CodeBuild nearly let attackers hijack trusted CI/CD pipelines.
The goal was simple: allow builds only from approved maintainers.
The mechanism? A regex checking the actor’s ID.
The problem? The regex matched substrings, not exact values. Without ^ and $ anchors, it asked:
“Does this string contain the approved actor anywhere?” instead of “Is this exactly the approved actor?”
The result:
- Attacker-controlled identities could bypass restrictions
- Protected pipelines could be triggered
- Secrets inside CI/CD environments were exposed
Two missing characters. A massive trust failure.

Why Regex Misconfigurations Are So Dangerous
Regex flaws break security in ways traditional defenses can’t see.
No Alerts
The system behaves “normally.”
Logs look clean.
Nothing crashes.
No Exploits
Attackers don’t inject payloads.
They simply fit the pattern.
No Malware
Everything happens within allowed logic paths.
This makes regex misconfigurations:
- Hard to detect
- Easy to exploit
- Perfect for supply chain attacks
How to Defend Against Regex-Based Security Failures
Design Principles
- Regex validates format, not identity
- Authorization must be explicit, not pattern-based
Implementation Rules
- Always anchor full matches
- Test against malicious edge cases
- Assume attackers will craft inputs to fit the regex
Operational Controls
- Code review regex like cryptographic logic
- Include regex abuse cases in threat models
- Monitor automation triggers aggressively
The Bigger Picture: Logic Is the New Attack Surface
Regex misconfigurations aren’t coding mistakes.
They are assumption failures.
They reveal a deeper truth about modern security:
Systems fail not when code breaks—but when trust is inferred.
As automation increases and security decisions move into configuration, logic becomes the weakest link.
And sometimes, all it takes is a missing ^ or $.
Final Thought
Firewalls can block traffic. Encryption can protect data. But regex decides who belongs.
And when that decision is wrong, everything downstream pays the price.
Security isn’t just about exploits anymore.
It’s about precision.


